Digital Security for Journalists
Even if you are not working on a sensitive story, you are a target if your colleagues are working on a sensitive story. Developing a strong security posture is paramount in the news industry. It not only affects you, it will affect the people around you.
Passwords vs Passphrases

When it comes to passwords, length is better than complexity. It important to switch your mindset to using passphrases, which are short sentences or rhymes that you can remember, instead of passwords.
While complexity—like adding symbols or numbers—is still important to an extent, every character added to a password will decrease the ability for a computer to guess it exponentially.
In a famous interview with Edward Snowden, John Oliver pokes fun at the apathy many people have with taking the time to change their passwords.
Password Managers
One common method of storing all of your passwords is to use a password manager. This is a piece of software that you can use to store all of your passwords in a single application. This way, every web service you sign up for can have a unique password, and you don’t have to remember them all. The password manager will assist you by generating random passwords when you create accounts for each web service online. It is recommended to use a password manager to store all of your passwords for every account you use online.
Popular Password Managers:
- 1Password — is a popular program, and offers a free service for journalists. For everyone else, it’s a subscription service.
- BitWarden — An open source service that has some free tiers for individuals.
- LastPass — LastPass
- Dashlane — DashLane
- KeePassX — A completely free open-source password manager. However, it’s less feature packed and less user friendly as others.
Most password managers have options to sync to an app on your phone, so you can always have access to your passwords wherever you are.
Single Point of Failure

One common concern about password managers is that it creates a single point of failure. Should someone get access to your password manager, they will have access to all your passwords! The reality is that it is still more secure to use a password manager than reusing the same password for multiple websites. The attack vector for getting access to a person’s password manager is far more difficult than finding compromised passwords online as a result of popular sites getting hacked.
Password Manager Code Word Trick
One trick to avoid the single-point-of-failure issue is to manually append a code word to all of your passwords as you type them into the login service. For example, you would come up with a memorable short word, like “battery.” Then, whenever you create a random password from your password manager and use it with a service, you would manually append this code to the end of the password.
fsdklfkasdlfaewgcxvzizqdfbattery
In the example above, you would copy the random password fsdklfkasdlfaewgcxvzizqdf from your password manager, but then manually type battery to the end. The battery code word would be something only you know from memory, and you would not store this into your password manager. This way, if your password manager is ever compromised, none of the passwords would work unless the adversary knew your code word.
(Alternatively, you can also prepend your code word to the beginning of passwords.)
2-Factor Authentication
Two factor authentication is among the best security practices and has a strong track records of preventing hacks. Many websites now support 2-factor authentication, it usually just takes a few extra steps to set it up. The two-factor process is relatively simple: You setup an app on your phone that has a code you type in to access a website, in addition to your standard password. This way, if your password is compromised, adversaries still cannot access your accounts without the codes on your phone. Two-factor authentication creates a secondary layer of security.
This website link above lists services that offer 2-factor authentication. Some popular 2-factor authentication apps include:

Duo is owned by Cisco, and allows for several different types of 2-factor authentication, including push authentication (when offered by the service).

Google Authenticator is an app run by Google that offers 2-factor codes.

Authy is another service, which offers back-ups of your authenticator codes in case you ever lose access to your phone.
Phishing and Spearphishing
By far, the most common way people get hacked is through some type of social engineering: getting people to inadvertently click on a link, responding to an email, or typing in their password into a website that isn’t what it purports to be. The practice of sending messages in order to trick users into a hacking attempt is called phishing. More advanced attacks that use a bit of social engineering — prior knowledge of the victim to get them to click a link in an email, for example — is called spearphishing. Spearphising would be, for example, receiving an email that purports to be from your boss asking to perform some familiar task. And the email would leverage some knowledge of your workplace based on information gleaned from the company website.
The best way to avoid these types of hacks is to stay vigilant and develop a strong security posture. Past examples have often shown that most of these attacks fail when users are alert, skeptical, and question whenever someone at their company sends them a link for any reason.
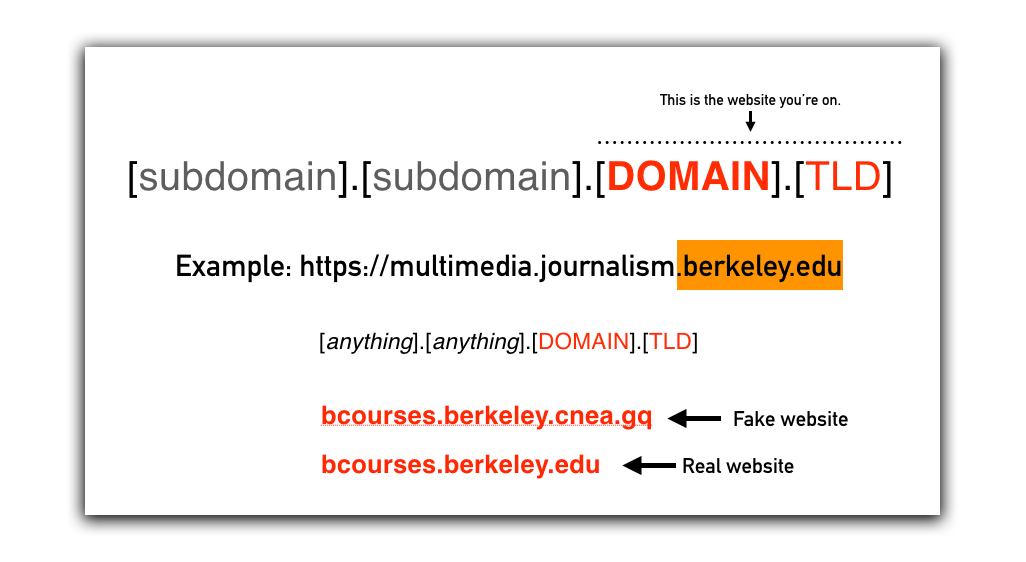
It’s also important to know when a link might be suspicious. The latter part of every URL is the domain and top-level domain. This is the actual website you’re visiting. Many attackers try to fool users by adding spurious subdomains to the URL.
Threat Modeling
Digital security involves a process called Threat Modeling. This is where you identify actual threats and take appropriate respective measures.
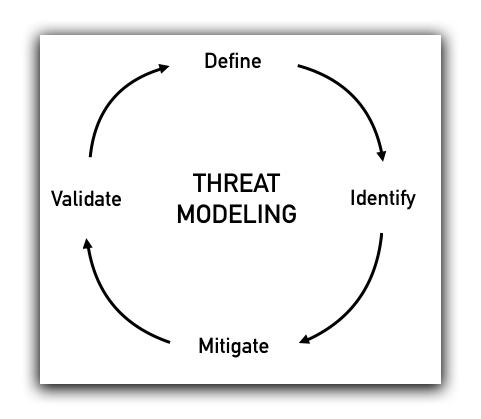
-
Define: What are your actual threats?
What exactly are you trying to prevent from happening? Getting hacked? Having a source identified by their employer? Protecting your privacy from online retailers? -
Identify: Who are your adversaries?
Who are your adversaries? What are their capabilities? Is it a stalker? An ex-boyfriend? The FBI or NSA? A foreign government? -
Mitigate: Minimize your threats.
Take steps to compartment your information to lessen the damage in worst case scenario. -
Validate: Check your decisions.
Study real-world scenarios similar to your situation, and learn from your own past experience.
This process is under appreciated. Many people don’t take commensurate measures based on actual threats. They either overshoot, needlessly taking extreme measures that stunt their ability to report freely. Or they don’t take ambitious enough actions given the capabilities of the threat actors involved. It’s a good idea to model various threat scenarios and look an prior examples for how you might mitigate these threats.
Threat Model Scenario: Meeting a friend for coffee
You’re at a coffee shop having lunch with a banker friend. She tells you, "There is some serious unethical stuff going on at our bank. It’s really sleazy. They're preying on elderly communities, signing them up with high-interest loans. The bank persuades them, when really it isn’t in their best interest. It’s not illegal per se. But it’s bad enough to make anyone’s stomach turn." The friend has a load of documents on her work computer proving these practices, including a video footage of seminars given in elderly communities. She wants to help you (a journalist) to get the word out.
Threat model this scenario.
- Define: What are the threats?
(The possibility of your source losing her job. Possibly getting sued by breaching NDA.) - Identify adversaries and their capabilities.
(The bank. Their IT dept can probably read all her emails from her work address. They can probably see actions taken on her work computer.) - Mitigate the threats.
(Don't speak too loudly at the cafe. Make sure she never contacts you via her work email, or sends documents via email. To get the materials, perhaps she can use a thumb drive, or better, take photos or video of her computer screen using a personal phone, or printing out documents, etc.) - Validate your decisions.
(What are similar situations? Where did things go wrong?)
Compartmentalize
It’s important to compartment your work into discrete silos. This helps to contain disaster when things go wrong. Some basic examples of compartmentalization include:
- Using burner phones — Many journalists will use burner phones to contact individual sources, so that it is separate from their typical work or personal phone. This can protect a source in situation if the phone records are subpoenaed (as what happened when the Justice Department subpoenaed Associated Press phone records to identify a whistle blower). It also protects the journalist when contacting potentially threatening individuals, such as criminal actors, gang leaders, etc.
- Using burner laptops - Many Chromebooks and other laptops are relatively cheap these days, some under $100. They do little more than email, but sufficient enough for working on an individual story. This way, if the laptop is compromised, the only damage is contained to that laptop.
- Using a different phone number — There are apps like MySudo that allow you to easily create unique phone numbers for different sources.
- Using different credit card numbers — Apps like Privacy.com allow you to create a new credit card number for each purchase, so retailers don’t have access to your purchase history.
- Using different social media accounts — Many journalists maintain separate social media accounts for their professional and private life, to maintain that separation from their work. As public figures, journalists often need to have a public persona and some don’t feel comfortable sharing private or family information in those venues.
There are many other examples of compartmentalization.
Tools

Tools are not magic. It is important to know when to use a tool, and what its limitations are. Never put all of your trust in any single tool, and always assume that a tool may be compromised. The best way to contain disaster in these situations is to compartmentalize your work. For example, when using an encrypted communication tool, use code words when arranging meetings. Or setup a separate account for separate sources. This way, if one account is compromised, it mitigates the damage to only that single source.
Signal

Signal is the de facto standard for secure messaging. It’s important to know that while the messages cannot be read in transit, they can be recovered from the individual phones at each end of the communication. One way to avoid this is to turn on disappearing messages, which automatically erase messages after a set period of time, and will affect both sides of the conversation.
VPN Services

Virtual Private Networks (VPN) are services you can use to mask your internet connection from the websites you visit. Every time you visit a website, the website can track where your connection originates, revealing information about both your connection and characteristics of your computer. A VPN can mask the connection origination to a different location. VPNs also create secure connections to the VPN service provider you use. This helps prevent hacking attempts when using public wifi, like at an airport of cafe. Anyone who intercepts your connection would only see encrypted traffic between your computer and the VPN provider.
See what websites know from your connection: https://browserleaks.com/ip
It’s important to note that VPNs do not ensure complete anonymity, and the VPN provider will be able to see the websites you visit. Many providers claim they don’t keep logs of the websites their users visit, however it is generally accepted by the security community that this is not true. Some popular VPN providers include:
TOR Browser

Tor is a special anonymous network of computers worldwide. When you connect to this Tor network, you’re completely anonymous when you visit websites.
There are certain websites that have the .onion at the end of their address that are only accessible via Tor. Sometimes called the Dark Web, these websites cannot track visitors and the location of their .onion web servers are hidden. These are sometimes a haven for illicit activity such as pirated content, pornography, or drug trafficking. Some Dark Web websites are used legitimately by activists and dissidents avoiding censorship from adversarial governments or other entities.
It’s important to note that while your connection to websites is anonymous, your local Internet Service Provider (ISP) that you use to connect to the internet can see that you’re connected to the Tor Network. In a famous case, a Harvard student attempted to use Tor to email a bomb threat to his university to get out of taking a test. He was caught in part because Harvard campus IT could see he was the only person on campus connected to Tor at the time the bomb threat was sent in.
PGP, GPG, or GnuPG

Pretty Good Privacy, or PGP, is a technology that allows for encrypting messages and files. It uses a system called public key encryption where users post a key publicly that anyone can use to encrypt messages, while the private key can be used to decrypt information. PGP is discouraged by many security professionals because of its complexity to use it effectively, and its single-point of failure. If the private key is compromised, all messages encrypted are thus compromised. Still, it maintains wide usage for specific purposes. In addition, PGP is often used to digital sign files and messages, to prove ownership.
The acronyms PGP, GPG and GnuPG are synonymous for the purposes of this tutorial and are often used interchangeably. A common community where people post their public keys and prove ownership is Keybase.io.
VeraCrypt

VeraCrypt is a software use for encrypting volumes (like a thumb drive, external hard drive, or a folder on your computer). It offers some advanced features including hidden volumes where it can hide files on a drive, made to appear like the drive is empty. It also offers plausible deniability, which is that the volume will have two passwords: one that would reveal decoy files, and a second, that will reveal the real files.
Mac Disk Utility

Macs come built-in with software for making encrypted volumes. While it doesn’t possess the range of features as VeraCrypt with hidden volumes or plausible deniability, it will allow you to encrypt a folder of files on your computer to protect them from adversaries. This method creates volumes that only work with other Mac computers.
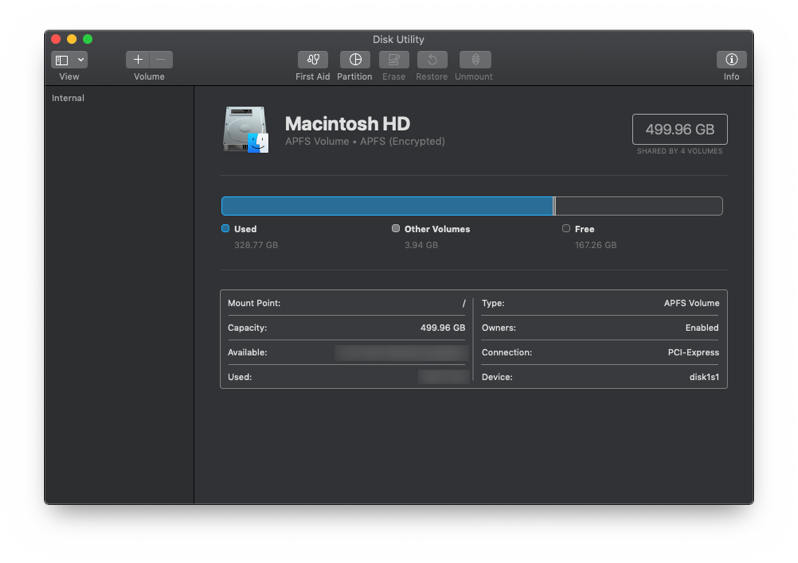
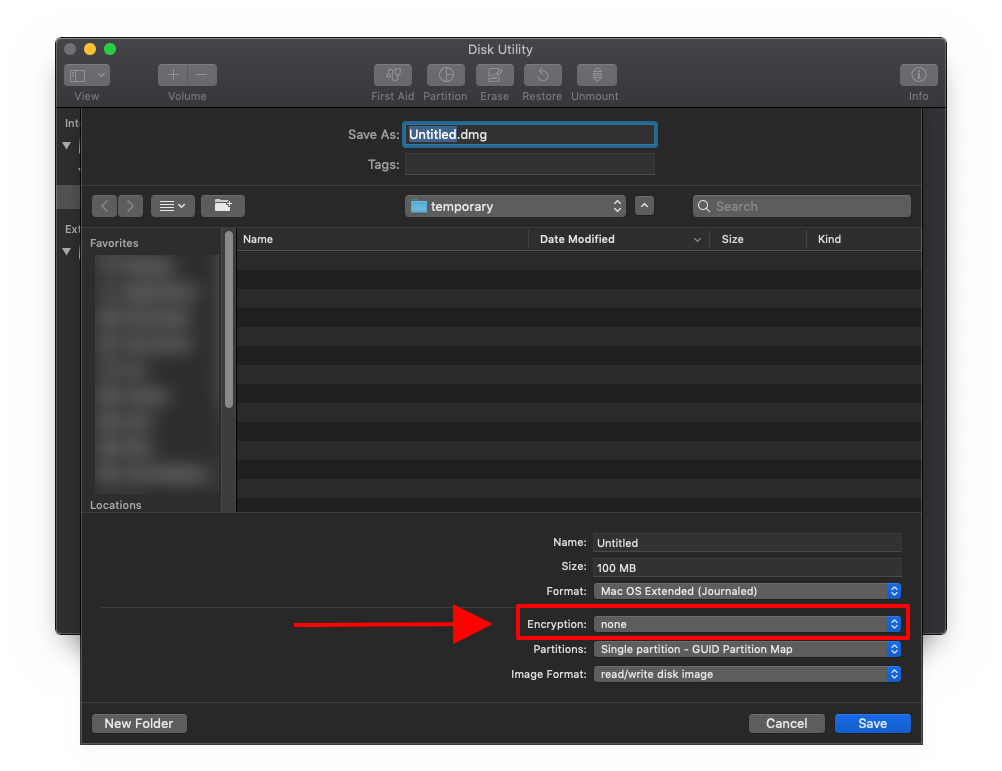
To create an encrypted volume:
- Open Disk Utility by searching for it on your computer
- Click File —> New Image (Blank Image)
- Set your encryption strength (higher is slower, but more effective)
- Set a size for the folder (called Volume). You can resize it later if needed.
This tutorial was written by Jeremy Rue.