Encryption
Caesar’s Cipher, The First Encryption
Among the first methods of encryption invented was called Caesar’s Cipher. This was rumored to have been used by Julius Caesar. It employs a very simple rule of shifting the letters and matching them to a second matching set:
Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher: XYZABCDEFGHIJKLMNOPQRSTUVW
Then to encrypt, the person looks up each corresponding value on the cipher for the message:
Plaintext: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG
Ciphertext: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD
In practice, many people have used decoder devices like this one:

Note: Caesar’s Cipher isn’t secure at all by today’s standards, and should never be used for any practical purposes.
Symmetric Encryption
Symmetric encryption is a type of encryption where both the person encrypting the message, and the message receiver, share a common key. You can think of a “key” similar to a password that can decrypt the message. In some situations, the key is a password.
An example of symmetric encryption can be done with GPG software, which can be installed with homebrew.
brew install gpg
gpg --armor --symmetric
You can then type in a message, and press control d to commit the message.
Another person, with GPG installed, can decrypt this message with the following command:
gpg --decrypt
Then paste in the encrypted message.
The downside with symmetric encryption is that you have to share the key with the other user. This seems practical if you have a personal relationship or an in-person meeting with the person. But if you wanted to encrypt a message for a random person
Public-Key Encryption (Asymmetric Encryption)
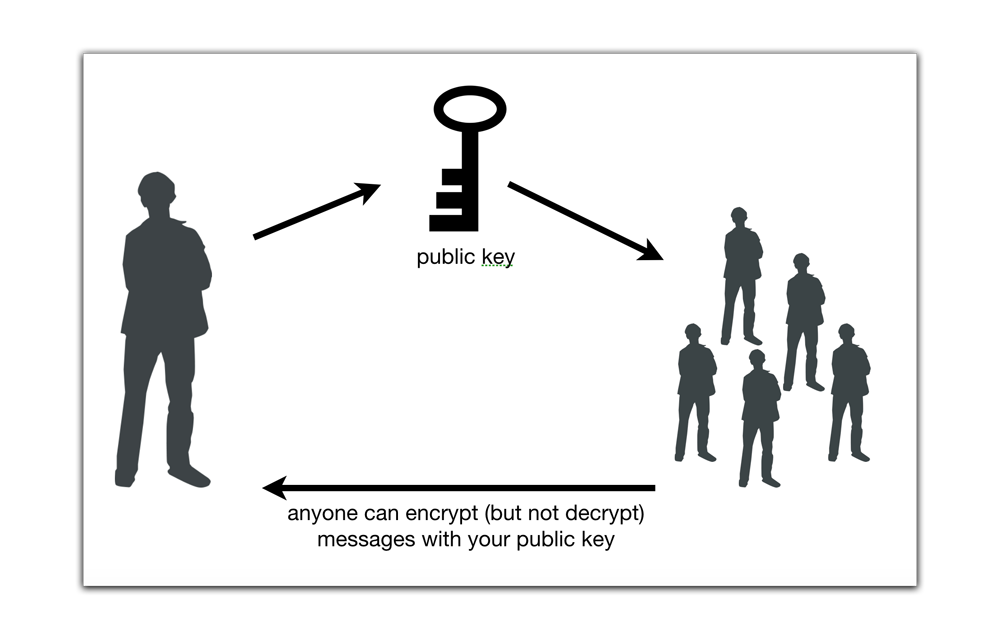
With Public Key Encryption, you don’t have to share a key with the other party. Each side has two keys, called a key-pair. One is a public key, and the other is a private key.
- Public key - This can be posted publicly for all the world to see. It can be used to encrypt messages.
- Private key - This is kept secret. It can be used to decrypt messages.
Using GPG, you need to first create a key pair.
gpg --full-generate-key
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Jeremy Rue
Email address: jrue@example.com
Comment:
You selected this USER-ID:
"Jeremy Rue <jrue@example.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
Once you’ve created the key, you can post the public key on a website like keybase.io or another public keyserver.
To get your public key, first list the keys you’ve created.
gpg --list-secret-keys --keyid-format LONG
/Users/hubot/.gnupg/secring.gpg
------------------------------------
sec 4096R/3AA5C34371567BD2 2016-03-10 [expires: 2017-03-10]
uid Hubot
ssb 4096R/42B317FD4BA89E7A 2016-03-10
Then take the key id (highlighted in the example above) and use it in the next command.
gpg --armor --export 3AA5C34371567BD2
This will list your public key. Later, if you want to encrypt messages for someone, you need to import their public key first.
gpg --import
Then paste their key. You can list all of the public keys from other users in your “keyring” using the following command. This will also show you the e-mail addresses associated with each key.
gpg --list-keys
To encrypt a message, use the following command:
gpg --armor --encrypt --recipient person@example.com
Type your message, and press control d to commit.
Digital Signing
Digital signing is a process of using a key to “sign” a file or some data, to prove that you had a private key.
In GPG, to sign some text use the following code:
gpg --clearsign
Then press control d
Diffie-Hellman Key Exchange
There is an important process in encryption called a Diffie-Hellman key exchange. It is a process that occurs every time you visit an https website. There are encryption keys built into your web browser that are automatically communicated with the website you’re visiting.
The following video explains the Diffie-Helman exchange is better detail.
Hashing functions
A hash is a cryptographic string that represents a sort-of signature for a piece of data, like a file or text. For example, the following text “hello world” generates the following has under the md5 algorithm.
md5 -s "Hello World"
MD5 ("Hello World") = b10a8db164e0754105b7a99be72e3fe5
Note: The MD5 algorithm is consider insecure, and is only being used in this example for its simplicity. A more secure implementation would be:
echo -n "Hello World" | openssl dgst -sha256
a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e
If we change even one character, or one byte of data, the hash would not match. This is true, even when we generate hashes for large files, or gigabytes of data. It’s a signature of sorts, to prove the data exists in a certain format. There are no keys to deal with, the hash is generated purely by the algorithm.
Hashing is often used for proving the integrity of a file, verifying that is hasn’t been tampered with. Another common use is to encrypt passwords so that the plaintext version never exists on a database in a server. Instead, when a user types in their password, the hash is compared to the one saved in the database.
But there are many other innovative uses people are designing along those lines.